Digital Wallets Security
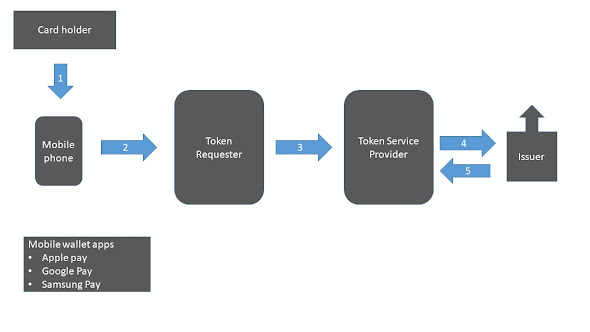
Introduction to digital wallets Digital wallet, also referred as "e-Wallet" allows people to perform electronic transactions without the need to have physical cards. Not only does it allows to perform payment and transactions, but also is handy to store other identity documents such as loyalty card(s) within the wallet. It also eliminates the need to carry multiple physical cards. Now as we have understood in simple words the meaning of digital wallets let us understand how do digital wallet transactions work. Steps of a digital wallet transaction being performed To use a digital wallet, the user needs to open the wallet application on mobile. To do this users can either use facial recognition, fingerprint identification, or PIN codes (based on the phone model and the configuration) Post unlocking the application, the user next selects the stored payment method for use, as digital wallets allows to store multiple cards There can be two type of transactions for digital wallet




