Stored XSS in Wonder CMS- CVE-2017-14522

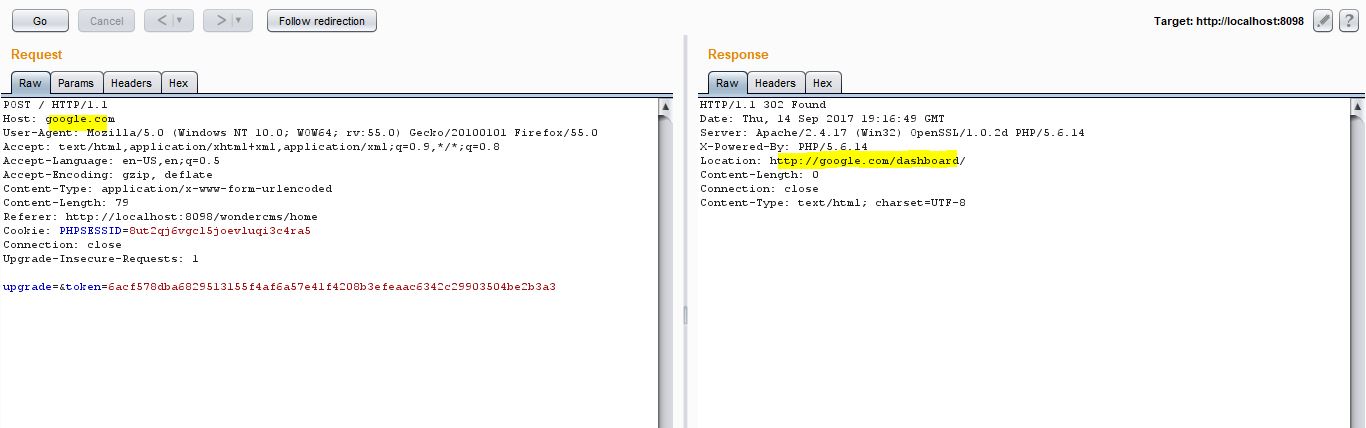
By- Samrat Das Hi Readers Recently in one of my pentest research, I found a CMS " WonderCMS" hosted in github. Curious to explore its functionalities, I downloaded and set it up in my local system. After fiddling with the source code, I found that it did not have any kind of security mechanism to filter any user input and accepted and stored in blindly without any sort of input validation Title of the Vulnerability: Stored XSS Common Vulnerability Scoring System: 7.0 Vulnerability Class: Injection Technical Details & Description: The application source code is coded in a way which allows user input values to be stored and processed by the application. CVE ID allocated : CVE-2017-14522 Product & Service Introduction: Wonder CMS 2.3.1 WonderCMS is an open source CMS (Content Management System) built with PHP, jQuery, HTML and CSS (Bootstrap responsive). WonderCMS doesn't require any configuration and can be simply unzipped a